CISA Zero Trust Maturity Model, Version 2.0, April 2023, page 7, U.S. Cybersecurity and Infrastructure Security Agency. Available at: https://www.cisa.gov/sites/default/files/2023-04/CISA_Zero_Trust_Maturity_Model_Version_2_508c.pdf.
As cyber threats become increasingly complex, the Zero Trust security approach offers a robust framework for safeguarding digital assets and providing secure network access. This blog explores the key concepts of Zero Trust, its fundamental pillars, and how agencies and organizations can utilize RUCKUS solutions to effectively implement this model to enhance their security posture.
Understanding Zero Trust
Zero Trust represents a foundational security philosophy that revolutionizes how organizations protect their networks and data. At its core, ZT operates on the principle of "never trust, always verify," marking a departure from traditional security paradigms that predominantly rely on perimeter defenses. Instead, it operates under the premise that threats can originate from both inside and outside of the network. This approach mandates continuous verification of the identity and integrity of every user and device, implementing strict access controls and providing comprehensive visibility across the network. It is not a specific product or solution but a mindset that fundamentally shifts how security is approached in the modern threat landscape.
The Zero Trust Architecture (ZTA) framework, detailed in NIST Special Publication 800-207, provides a structured method for embedding ZT principles into an organization’s network infrastructure. ZTA aims to minimize the attack surface through granular access controls and continuous network activity monitoring. By adhering to this framework, organizations can detect and mitigate potential threats in real-time, thus enhancing their overall security posture. Originally conceptualized by John Kindervag of Forrester in 2010, ZT builds upon established cybersecurity concepts such as least privilege, non-repudiation, and defense-in-depth. It emphasizes rigorous access controls and constant oversight to provide both security and usability for end-users
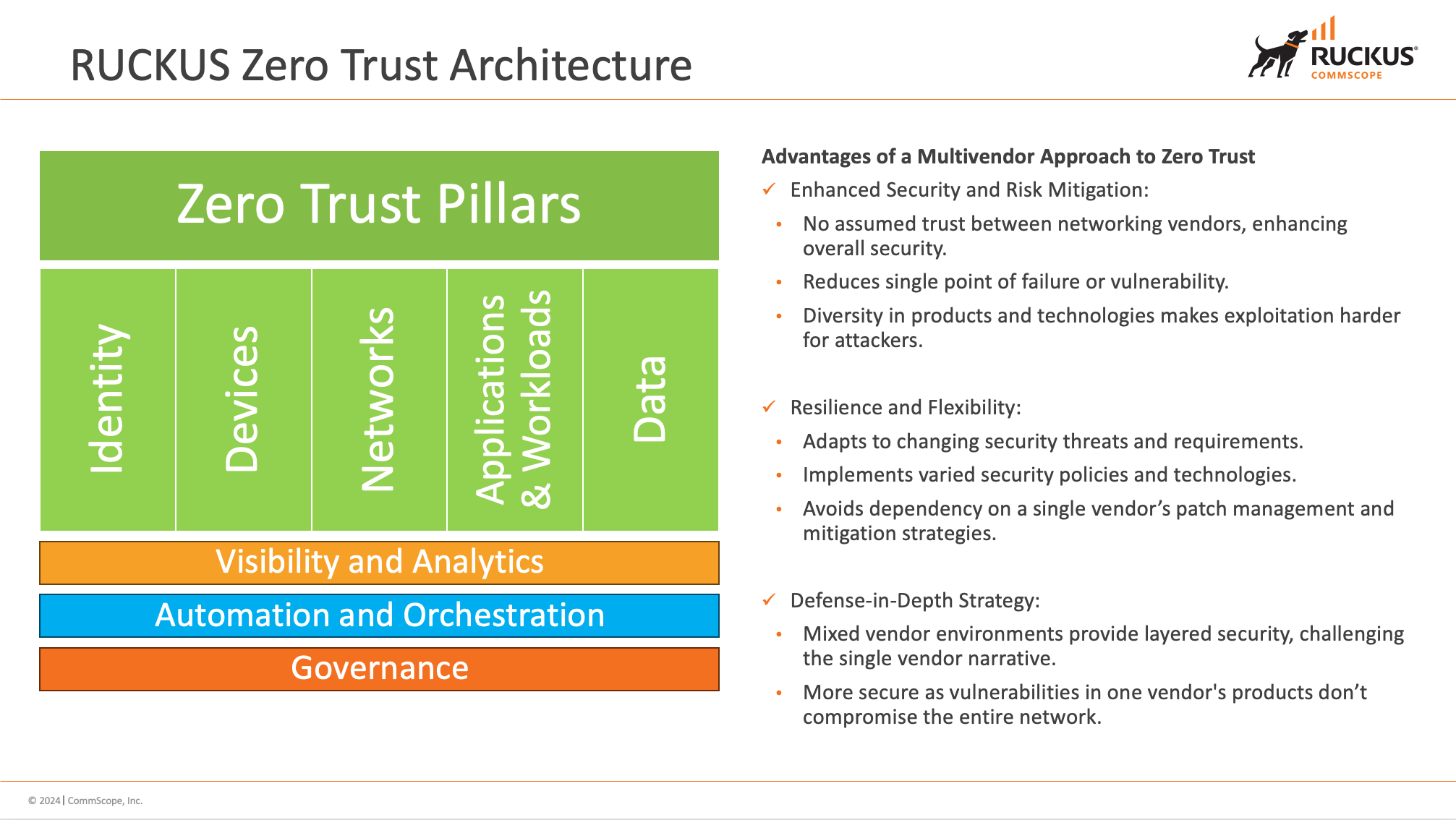
RUCKUS Networks exemplifies how modern networking solutions can seamlessly integrate with and enhance ZTAs. By supporting multivendor strategies, RUCKUS enables customers to leverage existing investments while adapting to a Zero Trust framework. This approach not only bolsters security but also maintains network efficiency and operational flexibility. As organizations move away from traditional security models, the adoption of ZTA requires reconfiguration of networking gear and a strong, collaborative relationship with networking partners. Through expertise and strategic implementation, RUCKUS aids in navigating this transition, reinforcing that Zero Trust is not just a technological shift but a crucial evolution in cybersecurity strategy.
The Five Pillars of Zero Trust
A critical component of successfully adopting Zero Trust is understanding and applying the "Five Pillars of Zero Trust." These pillars represent essential areas that organizations must focus on to enhance security and operational efficiency. Each pillar is underpinned by key capabilities that implement a comprehensive defense strategy and facilitate the seamless integration of Zero Trust principles into existing infrastructure.
1. Identity: Enforces strict verification and authorization of every user's identity before granting access to any resources.
- Traditional Approach: Perimeter-based identity verification using usernames and passwords only. Limited visibility and static reports on user identity and access patterns.
- Zero Trust Approach: Real-time visibility and dynamic updates using AI and machine learning for continuous identity verification and policy enforcement.
- Deployment Scenario: Identity verification using certificate-based authentication and Multi-Factor Authentication (MFA) to enhance security against credential-based attacks. (Find out more about RUCKUS’s Network Access & Policy Systems.)
2. Devices: Safeguards that all devices accessing the network are securely configured, managed, and continuously monitored for compliance.
- Traditional Approach: Reliance on endpoint protection with limited visibility into BYOD or unmanaged devices.
- Zero Trust Approach: Advanced analytics provide real-time visibility into device health and behavior, enabling compliance with security policies.
- Deployment Scenarios: Policy enforcement through automated device validation and access control, providing consistent security across all devices. (Find out more about RUCKUS’s Network Control & Management Solutions.)
3. Networks: Segments and analyzes traffic to limit movement and detect anomalies within the network.
- Traditional Approach: Focus on perimeter traffic with limited visibility into internal activities.
- Zero Trust Approach: Comprehensive visibility into all network traffic and microsegmentation to isolate network segments and enforce strict access controls.
- Deployment Scenarios: Implementing microsegmentation to prevent lateral movement of threats and applying least privilege access to minimize the risk of insider threats. (Find out more about RUCKUS’s Network Segmentation Solutions.)
4. Applications and Workloads: Secures application access, enabling only authorized users to interact with the applications.
- Traditional Approach: Application security with broad access rights and limited monitoring.
- Zero Trust Approach: Secure application access through granular controls and continuous monitoring, enabling only authorized access to critical applications and workloads, and behave predictably.
- Deployment Scenarios: Enforcing application-specific security policies and monitoring user interactions to detect and mitigate potential threats. (Find out more about the RUCKUS WAN Gateway.)
5. Data: Protects sensitive data utilizing encryption, strict access controls, and continuous monitoring to prevent unauthorized access and data leaks.
- Traditional Approach: Centralized data security with a focus on data-at-rest, and limited control over data movement and access.
- Zero Trust Approach: Protecting data through encryption, access controls, and monitoring data flows to prevent unauthorized access and data breaches.
- Deployment Scenarios: Implementing data protection strategies such as encrypting sensitive information to safeguard against breaches. (Find out more about Federal Certifications for the RUCKUS product portfolio.)
Your ZTA Journey Starts with RUCKUS
In the face of increasing cyber threats, adopting a Zero Trust model is essential for modern network security. ZT principles focus on continuous verification and strict access controls, enhancing protection and minimizing the risk of breaches. Our solutions are designed to align with these principles, offering advanced security measures that fortify your digital assets and contribute to your agency or organization’s sustained success.
This blog serves as a companion piece to the RTF Webinar, “Zero Trust: Defining Modern Network Security." Together, the webinar and blog provide a comprehensive introduction to ZT principles, emphasizing the importance of safeguarding your network in today’s evolving threat landscape.
Stay tuned for upcoming companion blogs that will provide actionable guidance on implementing Zero Trust, including integrating technologies like RUCKUS Cloudpath® enrollment system and RUCKUS Wan Gateway (RWG) to enhance identity management, MFA, and microsegmentation, as well as leveraging tools like RUCKUS AI™ for continuous monitoring and refinement of your Zero Trust practices.
Until then, discover how our Zero Trust solutions can help you build a secure and resilient network infrastructure. Check out the resources below for more information:
Whether you're just beginning your Zero Trust journey or looking for networking solutions to minimize latency within your ZTA, these resources, coupled with the expertise of RUCKUS systems engineers and partners, will empower you to successfully navigate this critical security transformation.
Get ahead with RUCKUS Networks!
Sign up for exclusive insights from RUCKUS Networks.
© 2024 CommScope, LLC. All rights reserved. CommScope and the CommScope logo are registered trademarks of CommScope and/or its affiliates in the U.S. and other countries. For additional trademark information, see https://www.commscope.com/trademarks. Wi-Fi is a trademark of the Wi-Fi Alliance. Bluetooth is a trademark of Bluetooth SIG, Inc. Zigbee is a trademark of the Connectivity Standards Alliance. All product names, trademarks and registered trademarks are property of their respective owners.